
Advance your competitive advantage with integrated payments & merchant services
Integrate your existing platform with Finvi's payments solution to provide flexible payment options including online, in-person, and text-to-pay. Let us handle the support, training, and security while you deliver frictionless, digital payment options to your clients.
Because Innovation Happens All Around
For those who push the boundaries of tech on all fronts, we are proud to partner with leading organizations across a number of industries, allowing our customers to build the foundation of their operations on Finvi.
Why Choose Finvi?

Automated Smart Workflows
Improve efficiency with intelligent, data-driven workflows that drive your ability to create scalable, repeatable processes.

AI & Machine Learning
Improve outreach with dynamic scoring and advanced segmentation, and ensure you're working accounts with the highest-potential yield.
Omnichannel Communications
Increase the likelihood of contact and speed of payments through modern communication and self-service channels.

Embedded Payments Processing
Eliminate the costs, delays, and risks associated with multiple vendors through a simplified, integrated payments solution.

Third-Party Integration
Supplement your Finvi platform with the add-ons that matter to your business through our growing third-party library.

Compliance
Improve your compliance processes-backed by Finvi's compliance expertise-by automating regulatory readiness directly into your workflow.
Find Your Path to Resolution
Request a Demo
Are you interested in learning more about the Finvi platform? Schedule a demo today.







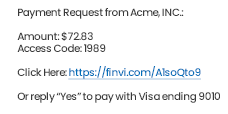
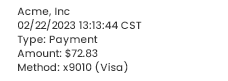


We know your business is complicated. That's why-based on Finvi's core workflow platform-we've thoughtfully designed our solutions to address the specific challenges of each industry we serve.
Not sure where to start? Let's talk. Our business consultants can get you started on your direct path to resolution.